1. Introduction
The Checkmk agent cannot be installed on some systems, and SNMP is not — satisfactorily --available. Nevertheless, Checkmk can still monitor such a system — as long as there is an application programming interface (API) with which Checkmk can retrieve the monitoring data. Such an API is usually based on Telnet, SSH or HTTP/XML.
You do not have to worry about querying these APIs yourself, because Checkmk supplies the necessary so-called data source programs for commonly implemented systems, for example for Amazon Web Services (AWS), Microsoft Azure and Google Cloud Platform (GCP), but also for NetApp, VMware ESXi, Prometheus, Elasticsearch, Cisco Meraki and many more. These programs generate agent outputs by querying hardware or software via a management API. They are also known as special agents, because they are a special alternative to the normal Checkmk agent.
2. Special agents in the Checkmk interface
Because special agents sometimes require quite complex parameters, we have defined special rule sets in the Setup GUI that allow you to configure them directly. You can find these rule sets grouped by use cases under Setup > Agents > VM, cloud, container and Setup > Agents > Other integrations:
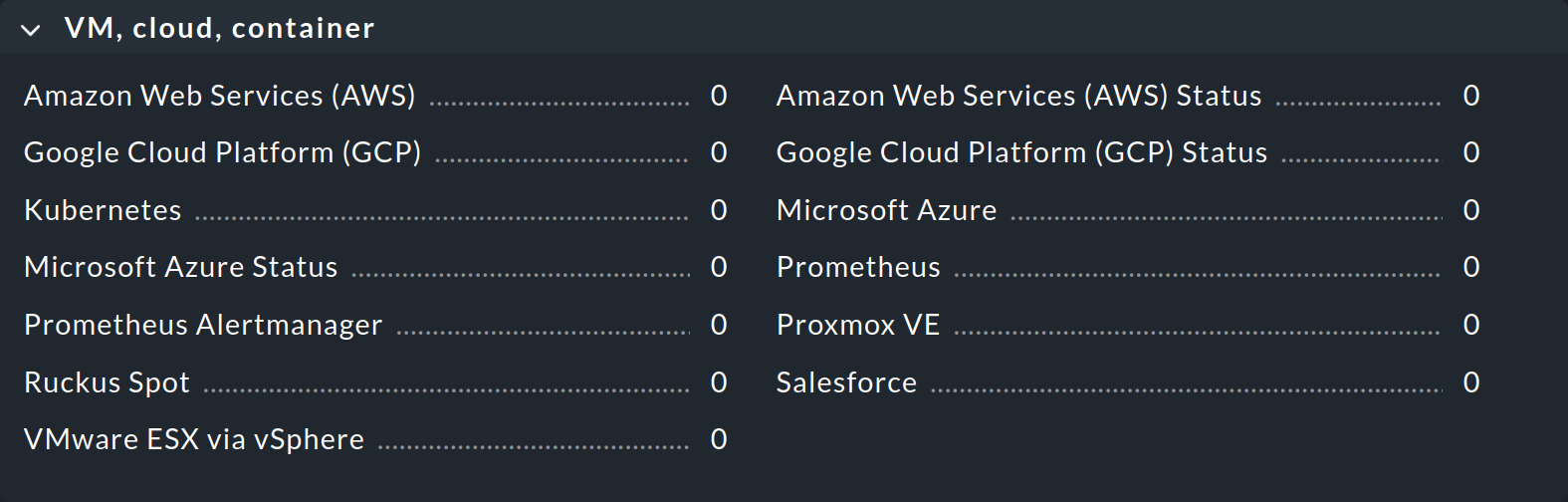
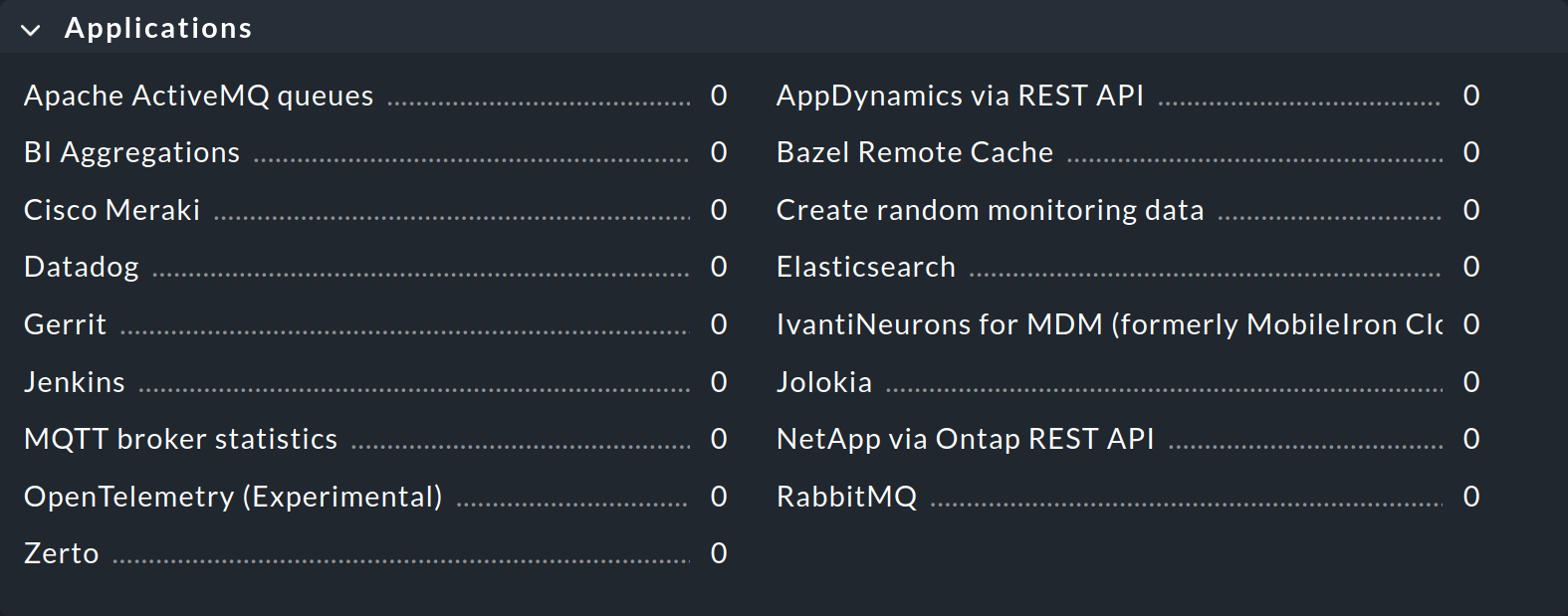
3. Using special agents
The special agents are installed under ~/share/check_mk/agents/special/.
If you wish to modify such an agent, first copy the file with the same name to ~/local/share/check_mk/agents/special/ and make your changes in that new version.
As an example, let us take the monitoring of NetApp Filers. These do not allow the installation of Checkmk agents. The SNMP interface is slow, flawed and incomplete. There is however a special HTTP interface which provides access to the NetApp Ontap operating system and all of its monitoring data.
The agent_netapp_ontap special agent accesses this interface via a REST API and is set up as a data source program using the NetApp via Ontap REST API rule set.
The data required by the special agent can then be entered into the rule’s content.
This is almost always some sort of access data.
With the NetApp special agent there is also an additional option for selecting the resources to be collected:
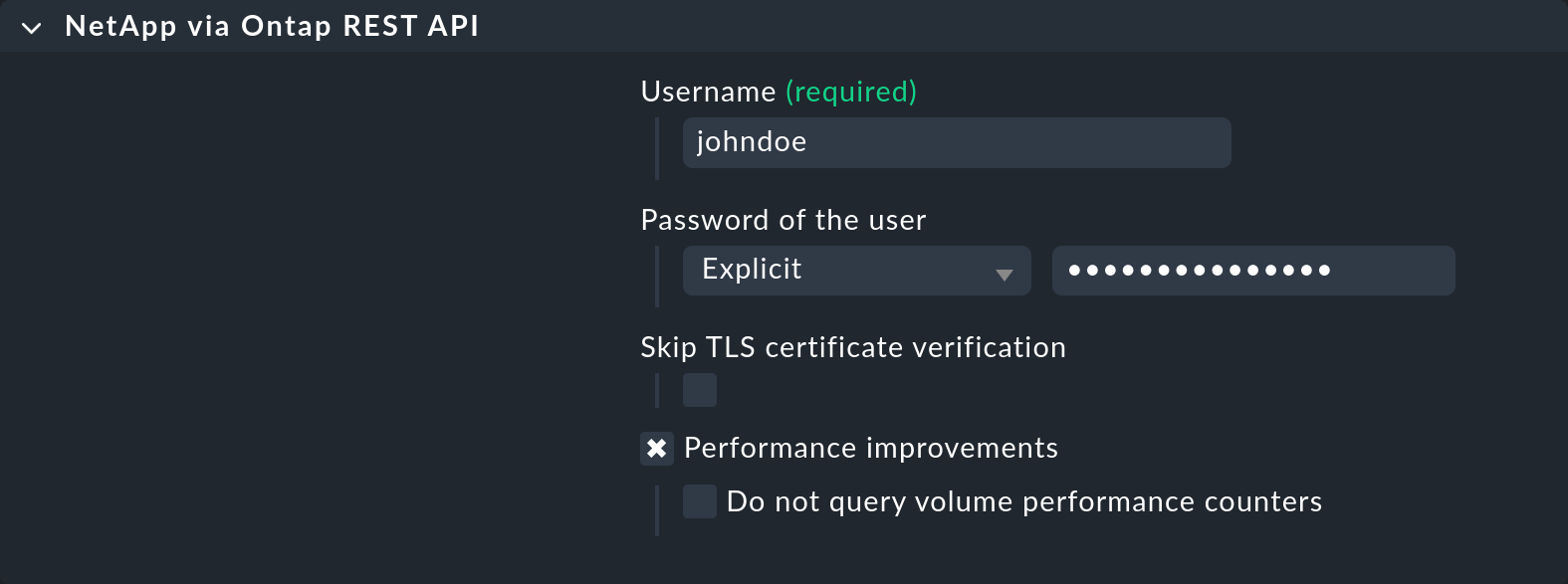
It is important that you leave the host set to API integrations if configured, else Checkmk agent in the Setup GUI.
There are occasions in which it is desired that both a special agent, as well as the normal agent are to be queried. An example for this is the monitoring of VMware ESXi over the vCenter. This latter is installed on a (usually virtual) Windows machine, on which reasonably enough a Checkmk agent is also running:
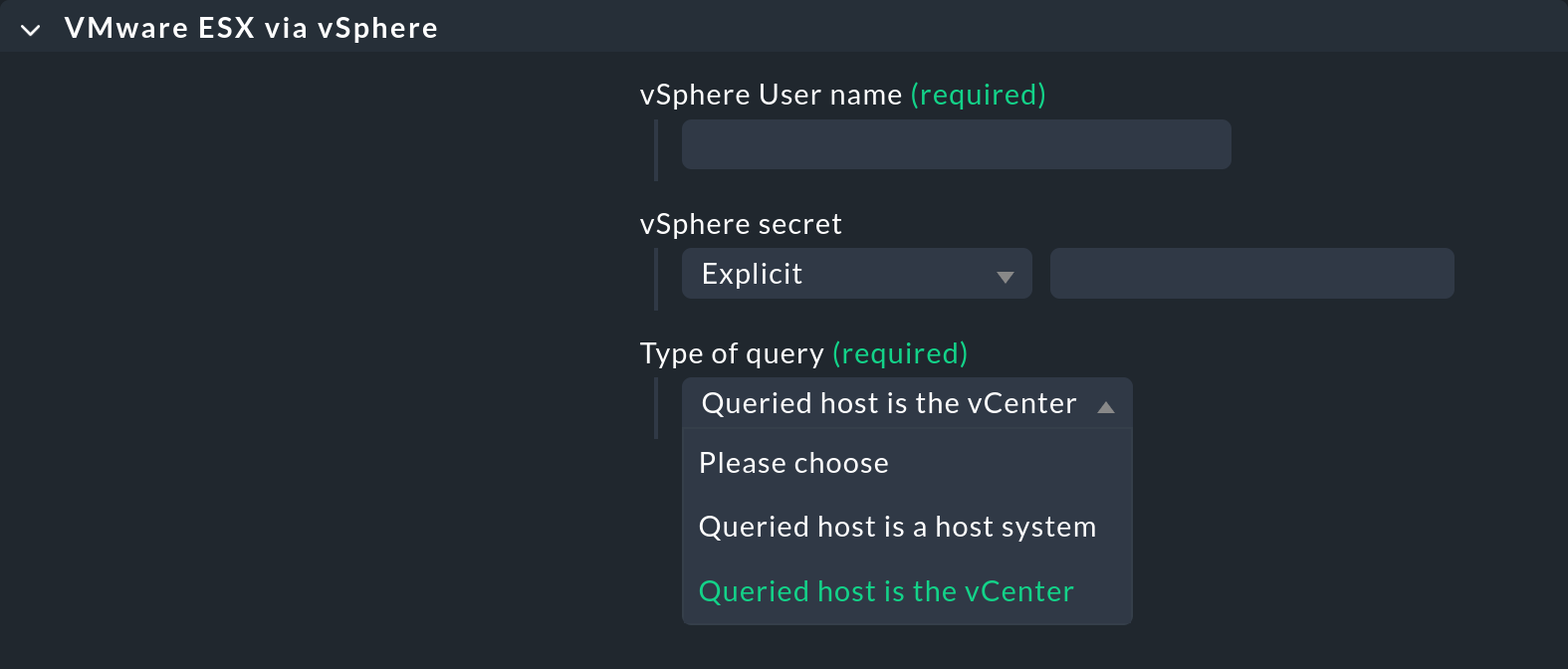
The configuration of important special agents is described in separate articles in this User Guide, for example for AWS, Microsoft Azure, GCP, Kubernetes, Prometheus, VMware ESXi and Datadog. |
4. Files and directories
| Path | Function |
|---|---|
|
The special agents provided with Checkmk are installed here. |
|
The repository for your own modified special agents. |
